Vendor: Canonical
Product: cloud-init
Category: CWE-200 Information Exposure
Version: v21.1 and below
Fixed: v21.1.19
CVE: CVE-2021-3429
Summary
Cloud-init enables engineers to automate operating system configuration, primarily within different cloud environments. Cloud-init can also function as a standalone configuration tool independent of any cloud provider.
Cloud-init includes an optional configuration module, chpasswd, which sets passwords for accounts on the underlying host system. Administrators can instruct cloud-init to set an administrator-defined password or to generate a random password at runtime. The module runs on the first system boot only (technically, the first boot which cloud-init is aware of) and does not run on subsequent boots.
The chpassword functionality is controlled by creating or modifying a cloud-init configuration file, located by default in the /etc/cloud/cloud.cfg.d/ directory. Cloud-init reads all files in this directory and applies configs in order of file read. For example, a configuration file with the following stanza would set the password “P@ssword!” for account bob:
chpasswd:
accounts: |
bob:P@ssword!To generate a random password at runtime instead of a static password, the ‘R’ or ‘RANDOM’ keywords are used in place of a password value. The following sample configuration creates a random password for bob:
chpasswd:
accounts: |
bob:RANDOMWith a random password applied, we must have some way of knowing what it was or the account becomes inaccessible for legitimate use! To solve this problem, cloud-init wrote all randomly generated passwords in cleartext to stderr, which sent them to the console during boot. Administrators could find and retrieve passwords from console output.
Here’s where the vulnerability popped up: cloud-init’s default logging configuration also redirected stdout and stderr to a world readable log file, /var/log/cloud-init-output.log . Any unauthorized, unprivileged user could view the cleartext password for any account which had a random password generated at runtime.
Grepping the log file for “password” as a non-root user and checking for lines surrounding keyword hits revealed any credentials:
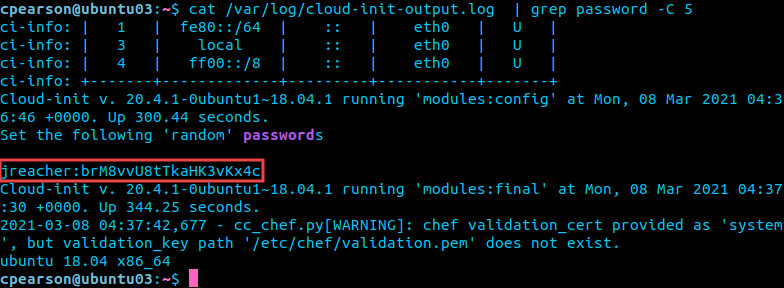
With credentials in hand, a malicious user could then move laterally on the local system. Only randomly generated passwords were leaked. Statically assigned passwords were not.
Patch
The change password configuration was updated to write randomly generated passwords to /dev/console instead of stderr. The change preserves printing passwords to console for administrator access, but without also writing the passwords to disk.
In addition, access to cloud-init-output.log is now restricted. Unprivileged users now cannot read the file. File permissions are changed on cloud-init upgrade; when you update cloud-init, the /var/log/cloud-init-output.log file permissions are modified.
Misc
Previously exposed passwords are partially protected with the permission change to the cloud-init-output.log file. However, if the file is copied anywhere, such as inside a system backup, anyone with access to the backup could potentially read the passwords.
If your cloud-init chpasswd config sets random passwords and also does not force password change on next login (by setting the ‘expire: false” option), then you really need to review your log file and accounts. In other words, if your chpasswd config looks like this:
chpasswd:
expire: false
accounts: |
alice:RANDOM
bob:RANDOM…then I highly recommend rotating each credential, or at least check if any leaked credentials grant access.
Finally, cloud-init is installed by default on some operating systems, including Ubuntu Server. While the vulnerable install base is therefore quite large, if chpassword functionality isn’t used, then the risk is effectively eliminated. You can’t leak passwords you’re not creating…
Kudos and thank you to the cloud-init team for promptly addressing the vulnerability and issuing a patch!
Thanks for reading! John 3:16
Reference:
https://ubuntu.com/security/CVE-2021-3429
https://bugs.launchpad.net/cloud-init/+bug/1918303